WireGuard is the latest addition to the VPN protocols. If you are wondering if WireGuard is worth the buzz, then you are not alone. Here is a review on WireGuard, covering all the aspects to understand it.
What you will see?
WireGuard VPN
The VPN companies construct and operate encrypted tunnels using a variety of protocols. This includes OpenVPN, IKEv2, L2TP, SSTP, and others. Each one of these has its own set of benefits and drawbacks. Although OpenVPN is the most common option, its initial design originates in 2001. And in all these 21 years much has evolved in our understanding of and use of the internet. WireGuard is a newer addition to the realm of VPN protocols. However, it’s already gaining traction in the cybersecurity community. Security researcher Jason A. Donenfeld, the protocol’s creator, started working on it in 2016. Although it was originally for Linux, it’s now accessible for Windows, Mac, Android, and iOS as well.
WireGuard has a number of advantages, one of which is its ease of use. While OpenVPN and IKEv2 both require hundreds of thousands of lines of code, WireGuard only requires about 5,000. This means that there will be fewer defects and security flaws. Reduction in the usage of CPU, as well as connection times, are shorter. It’s also better for routers and mobile devices that don’t have the processing capacity of a desktop computer. Another highlight is WireGuard’s use of cutting-edge cryptographic algorithms. This includes Curve25519, ChaCha20, Poly1305, and BLAKE2. The ability to run inside the Linux kernel, which is the heart of the OS and handles all the low-level heavy lifting.
Because OpenVPN runs outside of the kernel, Linux needs to perform additional work to assist OpenVPN in interacting with the system whenever it sends or receives packets. However, WireGuard runs inside the kernel, thus there’s no need to swap contexts. This results in a significant performance improvement.
Minimal WireGuard code base
WireGuard’s codebase is currently around 3,800 lines long. However, OpenVPN and OpenSSL have roughly 600,000 lines between them. With XFRM and StrongSwan combined, IPSec is also quite large. It has roughly 400,000 total lines. The benefits of having a smaller codebase are as follows:
- It is a lot simpler to audit. An audit of OpenVPN would take a large team several days. A single person can read WireGuard’s codebase in a few hours by one person.
- Auditing is easier when there are fewer vulnerabilities. This helps maintain WireGuard safe.
- In comparison to OpenVPN and IPSec, the attack surface is much lower.
- Enhanced performance
Performance improvements
VPN speeds might be a limiting factor for a variety of reasons. WireGuard is engineered to provide major performance enhancements. The combination of exceptionally fast cryptographic primitives and WireGuard VPN protocol being a part of the Linux kernel makes secure networking incredibly fast. It may be used in both small embedded devices such as smartphones and fully loaded routers. WireGuard can increase performance in the following areas:
- Faster speeds
- Better battery life with phones/tablets
- Better roaming support
- More reliability
- Faster at establishing connections/reconnections
Even mobile users using VPNs would find WireGuard useful. If your mobile device switches network interfaces, such as from WiFi to mobile/cell data, WireGuard maintains the connection as long as the VPN client sends authorized data to the VPN server.
Cross-platform ease of use
WireGuard VPN protocol functions properly across all main platforms, despite a slight delay in full deployment. Windows, Mac OS, Android, iOS, and Linux are all supported by WireGuard. Moreover, WireGuard employs public keys for authentication and encryption. Whereas OpenVPN relies on certificates. However, this causes several problems when using WireGuard as a VPN client. This includes problems like key generation and maintenance. A few VPN providers have already included complete WireGuard functionality in their VPN client assortment. You can consider NordVPN, Surfshark, and Mullvad as examples.
Merged into Linux and Windows kernels
WireGuard was formally incorporated in the 5.6 Linux kernel in March 2020. However, it was integrated into the Windows kernel in August 2021. WireGuard is also no longer in beta, with version 1.0+ available for practically every major operating system. It is currently stable and ready for wider usage as a result of these two advances. The WireGuard kernel module is available in all major Linux distributions’ package repositories, as well as certain specialized ones. WireGuard is one of the technologies that is built in by default starting with the Linux Kernel version 5.6. Because some distributions will continue to utilize earlier LTS (long-term support) kernels, being part of the Linux kernel will not immediately make WireGuard omnipresent. Although, embedded devices that could benefit from the technology, such as routers, are hesitant to embrace updated kernel versions.
The installable WireGuard module is already available for the OpenWRT community router firmware and EdgeOS. Since 2018, Donenfeld has been working on integrating WireGuard into the main Linux kernel. The merging was needed to make significant changes to both the Linux kernel’s cryptographic API and the networking stack. Donenfeld’s ideas included integrating Zinc, a new, simpler cryptographic API, into the Linux kernel. According to him, Zinc would make it easier for developers to execute cryptographic operations in their apps than the kernel’s current crypto API, which is too complicated for most use cases. However, another kernel developer later took up the task of incorporating most of the Zinc capabilities into the existing crypto API. Later, the kernel got improvements in November. The upstreaming of WireGuard into the Linux networking subsystem was aided by the integration of the Zinc cryptography primitives.
How does it work?
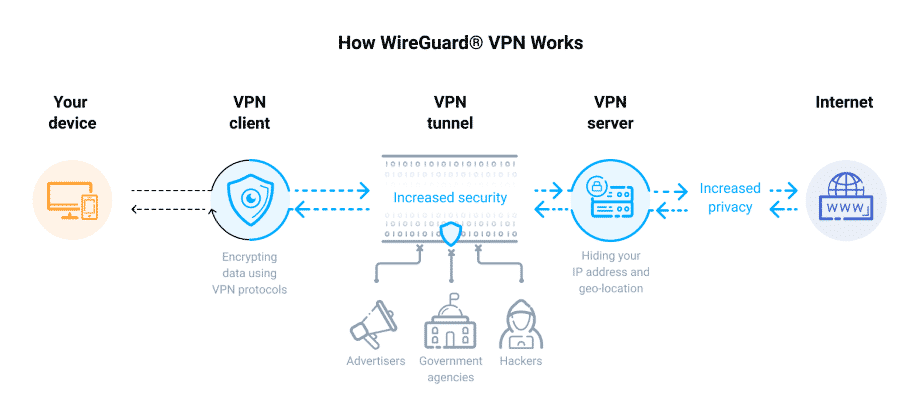
The WireGuard protocol eliminates cryptographic agility. It is the concept of allowing users to choose between multiple encryptions, key exchange, and hashing methods. Moreover, it even led to problematic deployments with previous solutions. Instead, the protocol employs a set of current, well-tested, and peer-reviewed cryptographic primitives. This resulted in secure default cryptographic choices that users cannot alter or misconfigure. If any severe flaws in the crypto primitives are uncovered, a new version of the protocol is released. Moreover, there is a way for peers to negotiate the protocol version.
WireGuard uses ChaCha20 for symmetric encryption and Poly1305 for message authentication. This is faster than AES on embedded CPU architectures without cryptographic hardware acceleration. Moreover, it uses Curve25519 for elliptic-curve Diffie-Hellman (ECDH) key agreement, BLAKE2s for hashing (faster than SHA-3), and a 1.5 Round Trip Time (1.5-RTT) handshake based on the Noise framework and provides forward secrecy. It also has built-in resistance against key impersonation, denial-of-service, replay attacks, and some post-quantum cryptography resilience. In this protocol, each peer is identifiable to others using short public keys, similar to how OpenSSH handles key-based authentication.
As part of a new concept called crypto key routing, the public keys are also utilized to determine which IP addresses are issued to each peer inside the tunnel. The protocol does not respond to packets from peers it does not recognize. So, a network scan will not disclose that WireGuard is operating on a machine. Furthermore, when there is no exchange in data, the connection between peers, which can work as both clients and servers at the same time, becomes silent.
Windows and a new TUN driver
Donenfeld and the other WireGuard developers have produced Wintun. It is a new, simpler open-source TUN driver that improves WireGuard performance on Windows. Windows do not have a native TUN virtual device. Although some drivers exist from projects like OpenVPN or SoftEther to do this. According to Donenfeld, these programs were created in a different period, the era of NDIS5, and then ported later to NDIS6. This means they haven’t benefited from features like NdisMediumIP in Windows 7, which allows for native layer 3 tunneling without the need for layer 2 emulations. Wintun’s design has the same emphasis on simplicity, suitability, and security as Zinc and WireGuard. OpenVPN developers are also working on adding support for OpenVPN so that it can take WireGuard onboard instead of the previous driver.
What is disappointing?
With all the great features and support, WireGuard is now widely popular in the VPN market. It’s already present in Surfshark, Private Internet Access, VyprVPN, StrongVPN, TorGuard, and others. Whereas, NordVPN’s NordLynx protocol is based on WireGuard. However, not every provider supports the technology, as VPN providers must address a number of difficulties before it can be implemented. This is because of some setbacks in WireGuard like the lack of the ability to assign dynamic IP addresses. This implies that your VPN IP address may remain the same each time you connect. So, it can potentially allow tracking of these addresses online. When you disconnect from WireGuard, your IP address is not automatically deleted.
OpenVPN and other protocols go above and beyond to preserve your privacy by destroying IP addresses when they’re no longer in action. Thus, lowering the chances of privacy breaches. There’s also no support for forwarding secrecy, which encrypts VPN data with a new private key for each session. By default, WireGuard utilizes the same key, which means that if a hacker gains access to the server and steals your key, he may be able to decode your communications as well.
WireGuard privacy problems
While WireGuard may provide efficiency and security advantages, it is still lacking in terms of privacy. This has caused many VPN providers to think about WireGuard’s privacy implications before getting it onboard. However, the problem has settled, and there are now some viable solutions to these issues. WireGuard is now a reliable VPN protocol, and a few VPNs have found efficient ways to implement it while maintaining customer privacy. IVPN did an excellent job of separating the two in order to comprehend the balance between privacy and security.
The protocol’s security is concerned with preventing attackers from gaining access to data in a tunnel, whether through breaking encryption, MITM attacks, or any other means, no matter how difficult. Privacy refers to whether or not an opponent may learn anything about you, your communications, or any parties with whom you’ve communicated. It has less to do with the data and more to do with the metadata. Even when security is impenetrable, privacy can be breached.
NordVPN double NAT system with WireGuard
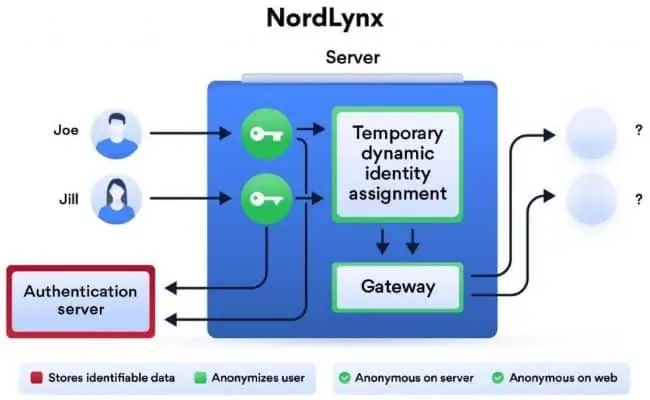
With NordLynx, NordVPN employs a Double NAT System, which is a unique approach to privacy challenges. The first interface assigns all users connected to a server a local IP address. Each user receives the same IP address, unlike the original WireGuard protocol. It activates the second network interface with a dynamic NAT system after establishing a VPN tunnel. Each tunnel gets its own IP address from the system. Internet packets do not mix up as they transit between the user and their targeted destination in this manner. Only while the session is active, dynamic local IP addresses are assigned.
Conclusion
Although there are privacy risks with WireGuard VPN protocol, they are not bugs or design flaws. The main idea behind WireGuard is to make things simple and remove a lot of the complications. Because the top VPNs have developed their own app and server-based solutions, these concerns do not imply that using WireGuard is less secure than using OpenVPN. Most of the VPN services have created their own different solution to resolve the privacy issue with WireGuard. IVPN has devised its own method of assigning dynamic IP addresses and providing you with a new private key. It also fixes the storing of IP addresses problem. It does so by detecting when your connection has been idle for three minutes and then deleting and reconfiguring your connection. Even with this complication, WireGuard offers the best performance.
What are your views on WireGuard? Tell us in the comments section below.
















