Phishing is a cybercrime where an objective or targets are reached by email, phone, or also text by somebody introducing as a genuine foundation to bring individuals into giving delicate data such as recognizable data, banking, and credit card details.
They then use this data to get to important accounts and can bring about identity theft and financial loss. Phishing attacks are the demonstration of sending fraudulent correspondences that seem to come from a trustworthy source. The goal is to assume delicate data like credit card and login information or install malware on the victim’s machine. Phishing is a typical sort of cyber attack that everybody ought to find out about to secure themselves.
What we will see here?
How does phishing work?
Phishing begins with a fraudulent email or other correspondence that is designed to bait a victim.
They make the message look like it comes from a trusted sender.
If that it tricks the person in question, they coax the individual to give secret data, regularly on a scam website. At times they make the malware download onto the target’s computer.
Phishing attack
Phishing is a kind of social engineering attack regularly used to take client information, including login credentials and also credit card numbers. It happens when an attacker, taking on the appearance of a confided in substance, dupes a victim into opening an email, text, or instant message.
They trick the beneficiary by making them click a malicious link, which can impel the installation of malware, the freezing of the system as a part of a ransomware attack, or the noteworthy of sensitive data.
An attack can have devastating results. For people, this incorporates unauthorized purchases, the taking of funds, or recognize theft.
An affiliation succumbing to such an attack ordinarily supports extreme financial in an extra declining market share, reputation, and client trust. Rely on scope, a phishing endeavour might develop into a security occasion from which a business will fight to recover.
Examples of phishing scams
The accompanying shows a typical phishing trick attempt:
- A spoofed email apparently from myuniversity.edu is mass-distributed to whatever number of employees could be allowed.
- The email guarantees that the user’s password is going to expire.
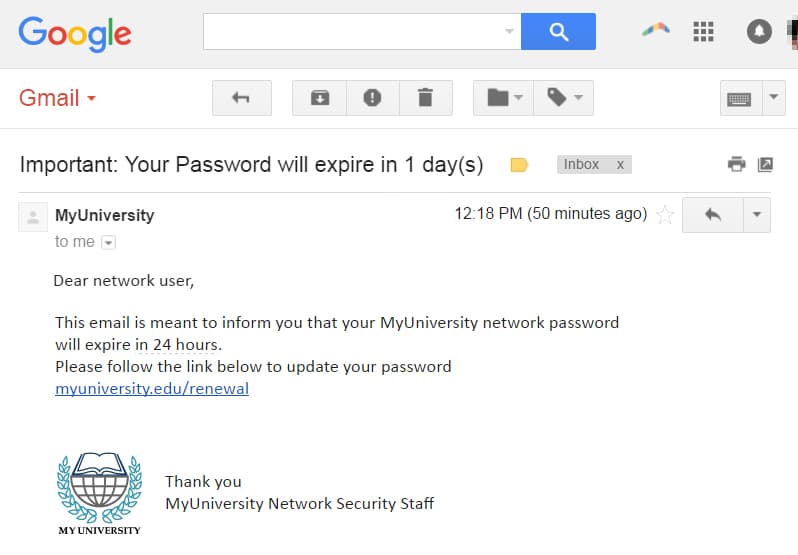
A few things can happen by tapping the link. For instance:
- The customer is redirected to myuniversity.edurenewal.com. The attacker, observing the page, hijacks the first password to access secured areas on the college organization.
- This results in a reflected XSS attack, giving the culprit restricted admittance to the college association.
Types of phishing
Spear phishing
Spear phishing focuses on a particular gathering or type of individual like an organization’s system administrators. If that you are going fishing with a pole, you could pull in an old boot, a fish, or a struggle any kind of fish. In case you are going fishing with a spear, you are picking a particular fish to follow. Henceforth the name.
Whaling phishing
Whaling is a much more targeted kind of phishing as it pursues the whales, the truly BIG fish. These attacks focus on the CEO, CFO, or any Cxx inside an industry or a particular business.
The connection takes you to a page where you are received some information about the organization, for example, tax ID and bank account numbers. Whaling is a mistaken name since whales are not really fish.
Smishing phishing

Smishing is an attack that utilizes text informing or short message service (SMS) to get your time. A message that comes into your phone through SMS that contains a link with a click or a phone number to call could achieve a smishing attack.
A situation that has played out ordinarily is an SMS that seems as though it is coming from your bank. It reveals to you your account has been compromised and you need to react right away. The attacker requests that you check your bank account number, SSN, and so on, Very much appreciate that the attacker has control of your bank account.
Vishing phishing

Vishing conveys a similar topic as the wide range of various phishing attacks. The attackers are as yet after your own data or delicate corporate data. They accomplish the attack by a voice call. Consequently the “v” instead of the “ph” in the name.
An exemplary vishing attack is a caller who professes to be from Microsoft and says you have a virus on your PC. You turn over Mastercard details to improve the version of anti-virus programming installed on your PC. The attacker currently has your Mastercard data and you have likely installed malware on your PC.
The malware could contain anything from a financial trojan to a bot (short for robot). The financial trojan watches your online exercises to take more details from you – this time your bank account information, including your password.
A bot is a piece of programming that will do whatever the hacker needs it to do.
It is controlled by command and control to dig for bitcoins, send spam, or dispatch an attack as a component of a distributed denial-of-service (DDoS) attack.
Email phishing
Email phishing is the most widely recognize kind of phishing. Hackers send these emails to any email addresses they can acquire. The email ordinarily tells you there has been a compromise to your account and that you need to react quickly by tapping on a given link. These attacks are normally simple to spot as the English aren’t clear. It can appear to be that somebody utilized a translation program and went through 5 different languages before showing up in English.
Another phishing trick referred to as sextortion, happens when a hacker sends you an email that appears to have come from you. The hacker claims to approach your email account and your PC. They guarantee to have your password and a recorded video of you.
The recorded video is the place where the sextortion part comes in. The hackers claim that you have been watching grown-up videos from your PC while the camera was on and recording. The interest is that you pay them, ordinarily in bitcoin, or they will deliver the video to family or partners.
Search engine phishing

Search engine phishing, otherwise called SEO poisoning or SEO trojans, is the place where hackers work to turn into the top hit on a search utilizing Google or different engines. If that they can get you to tap on their link, it takes you to the hacker’s site. At the point when you connect with it and enter sensitive information, they have your data. Hacker sites can act as any sort of site, however, the excellent candidates are banks, PayPal, web-based media, and shopping sites.
How to protect youself against phishing attacks?
Knowledge and education
One approach to shield yourself from phishing is user education. Education ought to include all workers. High-level leaders are frequently objective. Show them how to perceive a phishing email and what to do when they receive one. Simulation exercises are additionally key for surveying how your workers respond to an organized phishing attack.
Security technology
No single cybersecurity technology can forestall phishing attacks. All things considered, networks should adopt a layered strategy to reduce the number of attacks. Network security technologies that ought to be executed include email and web security, malware protection, user behaviour checking, and access control.
Identifying Signs of a phishing scam
The best assurance is awareness and education. Try not to open connections or links in unsolicited emails, regardless of whether the emails came from a recognized source. If that the email is surprising, be careful about opening the attachment and check the URL.
Enterprises ought to educate and prepare their employees to be careful about any communication that requests individual or financial data. They ought to likewise instruct employees to report the danger to the organization’s security tasks group right away.
Here are a few indications of a phishing scam:
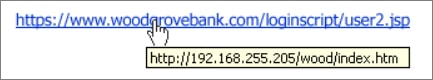
- The associations or URLs gave in emails are not highlighting the right area or are highlighting an third-party site not identified with the sender of the email.
- For instance, in the picture below the URL given does not coordinate with the URL that you will be taken to.
- There’s a request for personal information such as social security numbers or bank or financial data. Official communications will not by and large request personal data from you as an email.
- You receive message – unexpected and unsolicited. If that you suddenly get an email from an element or an individual you seldon manage, consider this email suspect.
- The message or the connection asks you to enable macros, adjust security settings, or install applications. Typical emails will not request that you do this.
- The message contains errors. Legitimate corporate messages are more averse to have typographic or grammatical errors or contain wrong data.
- The sender’s address doesn’t match the signature on the actual message.
There are multiple recipients in the “To” field and they give off random addresses. They send the Corporate messages straightforwardly to singular recipients.
- The greeting on the actual message doesn’t personally address you. Aside from messages that mistakenly address an alternate person, greetings that abuse your name or pull your name straightforwardly from your email address tend to be malicious.
- The site looks natural yet there are inconsistencies or things that aren’t quite right. Warning signs incorporate outdated logos, request that users give extra data that is not ask by real sign-in sites.
- The page that opens is not a live page, yetthey design a picture to seem as though the site you know about. A spring-up may create a request credentials.
Software solutions for organizations
- Microsoft Edge and Windows Defender Application Guard offer security from the expanding threat of targeted attacks utilizing Microsoft’s industry-leading Hyper-V virtualization innovation.
- If that a browse site is considered untrusted, the Hyper-V container will isolate that gadget from the remainder of your organization along these lines forestalling admittance to your enterprise information.
- Microsoft Exchange Online Protection (EOP) offers enterprise-class dependability and protection against spam and also malware while keeping up with admittance to email during and after emergencies.
- Utilizing different layers of filtering, EOP can give various controls to spam filtering.
- For example, bulk mail controls and international spam, that will additionally improve your protection services.
- Use Microsoft Defender for Office 365 to assist with protect your email, files, and online storage against malware. It offers all comprehensive protection in Microsoft Teams, Word, Excel, PowerPoint, Visio, and more.
- By ensuring against unsafe connections and also expanding assurance against malicious link, it complements the security highlights of Exchange Online Protection to give better zero-day protection.
Phishing attack protection require steps to be taken by the two users and ventures.
For users, vigilance is key. A spoofed message regularly contains subtle missteps that uncover its actual character. These can incorporate spelling mistakes or changes to domain names, as found in the previous URL example. Users ought to likewise stop and think about why they’re in any event, getting such an email.
For enterprises, various advances can be taken to mitigate both phishing and also spear-phishing attacks:
- Two-factor authentication (2FA) is the best strategy for countering phishing attacks, as it adds an additional verification layer when logging in to sensitive apps. 2FA depends on users having two things: something they know, for example, a password and also a user name, and something they have, for example, their smartphones. In any event, when worker are compromise, 2FA prevents the utilization of their compromised credentials, since these alone are inadequate to acquire passage.
- As well as utilizing 2FA, associations ought to enforce strict password management arrangements. For instance, employees ought to be needed to frequently change their passwords . And also not to be permitted to reuse a password for various apps.
- Instructive missions can moreover help to diminish the threat of phishing attacks . And you can do this by approving secure practices, for instance, not tapping on external email links.
Conclusion
Phishing attacks can have an incredible scope of targets relying upon the attacker. They could be conventional phishing emails searching for any individual who has a PayPal account.
The attacker takes incredible consideration to create the email, generally in light of the access they have. If that the email is at this end of the range, it is very challenging for even the wariest not to fall prey to it. Insights show that 91% of data security breaks start with a phishing plan of some kind.
Read more!
- iPad 2 Wallet Case-Best for keeping your cards, money essentials, etc.
- Language Translation Device-All the basics you need to know!
- How to add your bank account to your Apple card payment option?
- Changing email account settings for iPhone and iPad!
- iCloud Photo Library and Security- All you need to know about securing your storage!
















